Design of the Encrypted Messaging functionality in the
Android 4.4.4 "KitKat" hardened binary distribution
by Guido Trentalancia
The existing messaging functionality in the original Android KitKat distribution
was designed as depicted in the figure below.
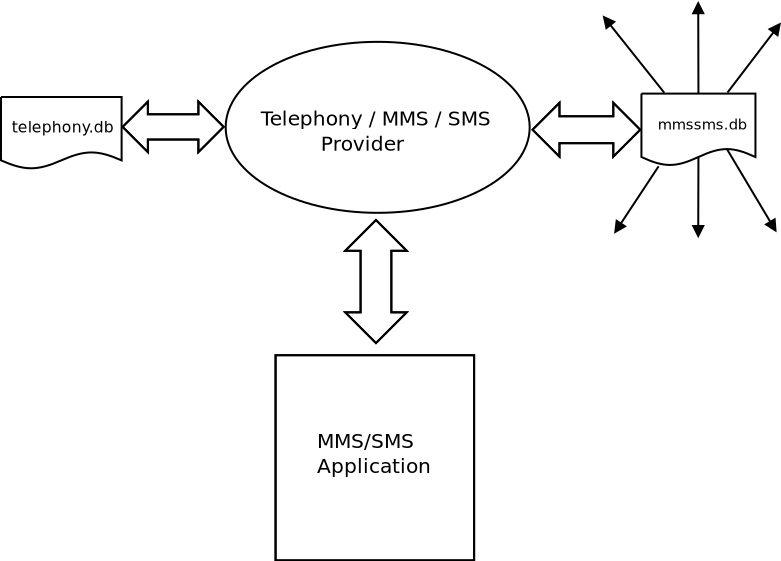
The MMS/SMS Application uses a combined Telephony and Messaging Provider, which
in turn makes use of two external databases telephony.db and mmssms.db
to store phone calls and text messages.
The MMS/SMS Database used to have a rather generic SELinux label and could be
accessed by several SELinux domains (including all applications) and therefore,
if one of such domains was compromised, the confidentiality of all sent and
received text messages was lost.
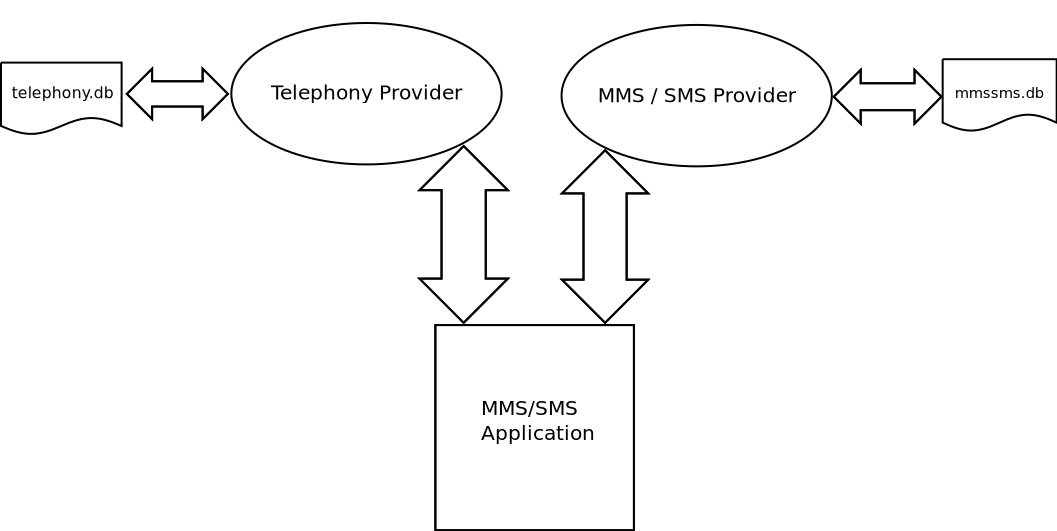
In order to safeguard the confidentiality of the MMS/SMS Database, the framework
has been redesigned as follows: the Provider has been split into a Telephony
Provider and a MMS/SMS Provider, the MMS/SMS Application has been assigned a new
SELinux domain shared only with the MMS/SMS Provider, so that they both run in
a separate dedicated SELinux context, which has exclusive access to the MMS/SMS
Database, with the latter being labeled using a specific rather than generic
SELinux label. The new design is depicted in the figure below, from which it
should be evident that the MMS/SMS Database is no longer accessible by entities
other than the MMS/SMS Provider and indirectly by the MMS/SMS Application.
This additional layer of all-round Operating System hardening complements over-the-air cryptography.
Now let's start a shell on the device and verify that the new architecture has been properly implemented and that it running effectively:
linux-pc$ adb shell
* daemon not running. starting it now on port 5037 *
* daemon started successfully *
shell@android:/ $ ps -Z | grep com.android.mms
u:r:mms_app:s0 mmssms 1173 245 com.android.mms
u:r:mms_app:s0:c512,c768 u0_a8 1369 245 com.android.mms
shell@android:/ $ ps -Z | grep mms_app
u:r:mms_app:s0 mmssms 1173 245 com.android.mms
u:r:mms_app:s0:c512,c768 u0_a8 1369 245 com.android.mms
shell@android:/ $ ls -lZ /data/data/com.android.providers.messaging/databases/mmssms.db
/data/data/com.android.providers.messaging/databases/mmssms.db: Permission denied
shell@android:/ $ dmesg | grep denied
...
type=1400 audit: avc: denied { search } for comm="ls" name="com.android.providers.messaging" dev="mmcblk0p24" scontext=u:r:shell:s0 tcontext=u:object_r:mms_data_file:s0 tclass=dir
shell@android:/ $ ls -lZ /data/data/com.android.providers.telephony/databases/telephony.db
/data/data/com.android.providers.telephony/databases/telephony.db: Permission denied
shell@android:/ $ dmesg | grep denied
...
type=1400 audit: avc: denied { search } for comm="ls" name="com.android.providers.telephony" dev="mmcblk0p24" scontext=u:r:shell:s0 tcontext=u:object_r:radio_data_file:s0 tclass=dir
From the output of the first Android shell command, we can conclude that both the MMS/SMS Provider (first process) and the MMS/SMS Application (second process) are running in a new mms_app SELinux context.
From the output of the second Android shell command, we can conclude that the MMS/SMS Provider and the MMS/SMS Application are the only two processes running in the new mms_app SELinux context.
The output of the third Android shell command cannot be shown due to SELinux restrictions on the shell process ("Permission denied" error), however we can use a trick and show the SELinux denials from the kernel log (output of the fourth Android shell dmesg command).
Indeed, the last line of the dmesg output shows that the /data/data/com.android.providers.messaging directory is correctly labeled with the new file type mms_data_file (and that consequently, when a new file or directory is created in such directory, its label is inherited from its parent directory).
The fifth and sixth tests performed using the Android shell confirm that the /data/data/com.android.providers.telephony directory (and all files and directories within it) are labeled with a different SELinux file type radio_data_file.
As already noted, the new mms_data_file file type can only be accessed by the new mms_app SELinux domain, so the MMS/SMS Database /data/data/com.android.providers.messaging/databases/mmssms.db is now secured.
Exercise
The new architecture which splits the Telephony and MMS/SMS Providers and which protects the MMS/SMS Application using a new SELinux domain was introduced in year 2025. Perform again the above mentioned steps on any version dated before year 2025 and verify that older versions (original Android architecture) do not protect the MMS/SMS Application and Database.
The Android 4.4.4 "KitKat" OS hardened binary distribution for the Sony Xperia E3 (D2203, D2206, D2243, D2202) devices is available here: Android 4.4.4 KitKat hardened binary distribution
Android is Copyright (C) 2007-2025 by the Android Open Source Project
and is a trademark of Google Inc.
Xperia is a trademark of Sony Mobile Communications Inc.
Copyright © 2007-2025 Guido Trentalancia. All rights reserved.


